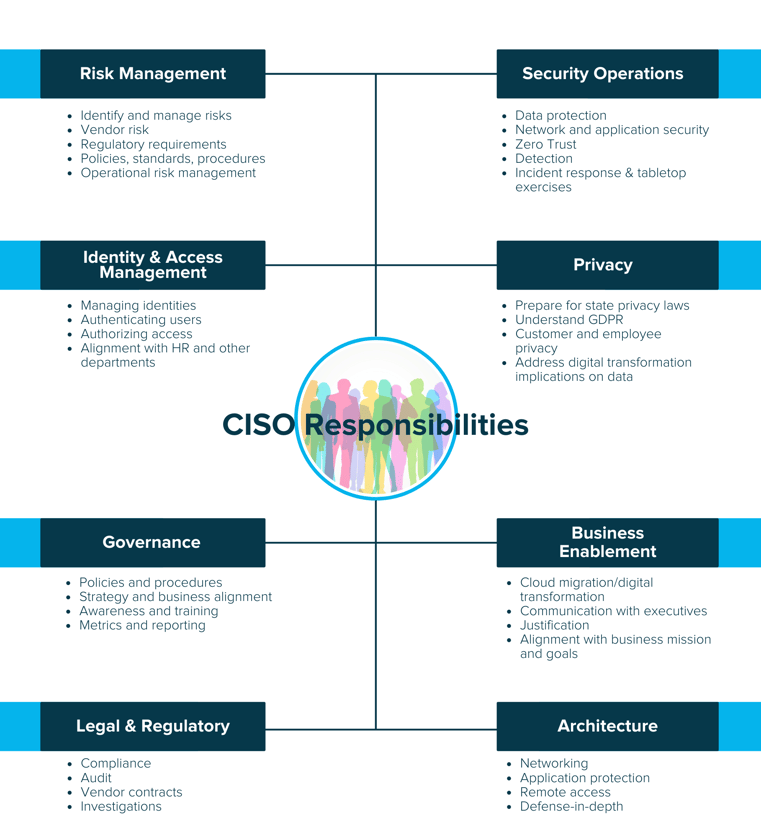
In this issue of the magazine, we interview effective security leaders with deep expertise building and maintaining robust, proactive security programs. While their leadership styles may vary, the approach they take to a strong program is similar – they focus on building programs directly aligned to business goals to ensure they make a positive impact and reduce risk.
We found that no two programs look the same in terms of structure, responsibilities, or team. Below we share snippets from the security leader’s profiles:
HEALTHCARE
Page 4 - Dan Bowden, CISO, Sentara Healthcare
Dan Bowden, CISO, Sentara Health organizes his program into three areas: enterprise cybersecurity, enterprise cyber risk, and enterprise identity services. He plans to have directors oversee each of these areas, with a team to execute on core goals. Bowden says, “That’s how I’m going to organize my team strategically going through 2022 and the upcoming years is those three directors. And as we develop the amount of work, what drives work, what creates work, how do we prioritize things, that will then inform how we model the teams that report to them. I delegate a lot. I ask a lot of questions. How is work getting done? How is performance being managed? But for the most part, I don’t really tell the directors specifically how to model their teams. The next couple of years will be interesting because we’ll be changing our org model a little bit, and we will be increasing the total breadth of the services that we offer to the organization.”
INSURANCE
Page 14 – Jon Fredrickson, Chief Risk Officer, Blue Cross & Blue Shield of Rhode Island
When Fredrickson first started at BCBSRI as Information Security Officer (ISO), he oversaw the information assurance program, comprised of a team responsible for governance, risk and compliance, some incident response, and threat intelligence with limited technical responsibilities. Shortly after, he added the title of HIPAA Privacy Officer because of his extensive experience working in healthcare. Then, security operations was brought in under him, along with enterprise risk management and most recently business continuity. He has since transitioned from CISO to CRO, now responsible for the entire risk portfolio. Today, his programs include enterprise risk management, business continuity, information assurance, security operations, and privacy.
SOFTWARE
Page 10 – Billy Spears, CISO, Alteryx
Billy Spears looks at his security department from a functional perspective, with the traditional information security side, along with the cybersecurity side of the organization.
The information security side includes governance, risk, and compliance. Spears explains, “We have programs like program management and underneath that, training, awareness, policies and similar things. We also have our compliance functions. This is the review function, audit function, and regular analysis to understand where you are versus where you think you need to be. And then risk management assesses the rank and stack of that.”
On the other side, the cybersecurity organization provides services to two different areas – the enterprise side and the software or product side. Spears says, “The enterprise is your traditional core company. That’s the front-end of the house to make the company work. It’s your network, your infrastructure, your marketing, those kinds of things.”
He continues, “The product side is composed of the product or the design for what we want to build. And then that goes over to the engineers. Those are the folks that actually build the technology. And then you have the customer team that works with customers and communicates and helps the process move forward. Product security is heavily involved in most of those areas, and then we support the customer team in their interactions with the customers.”
FINANCE
Page 16 – Sean Kearney, CISO, Natixis CIB Americas
Sean Kearney says, “I lead the second line of defense security risk management team, which provides direction and oversight to all technology and security operations, ranging from patch and vulnerability management to antimalware coverage, from identity and access management to secure development practices. My team and I provide the oversight and monitoring of how effectively these areas, and the controls within them, are performed. My role in a nutshell is to make sure that information security, IT security and anything related to that space is performed appropriately. I do that by owning and managing the cybersecurity program which is made up of a number of different policies and risk management processes including a robust control framework to monitor and test all key technical controls.”