Managed Threat Intelligence Service (MANTIS)
A mature threat intelligence program that enables organizations to proactively protect their data and customers, make smarter decisions, and strengthen their overall defenses
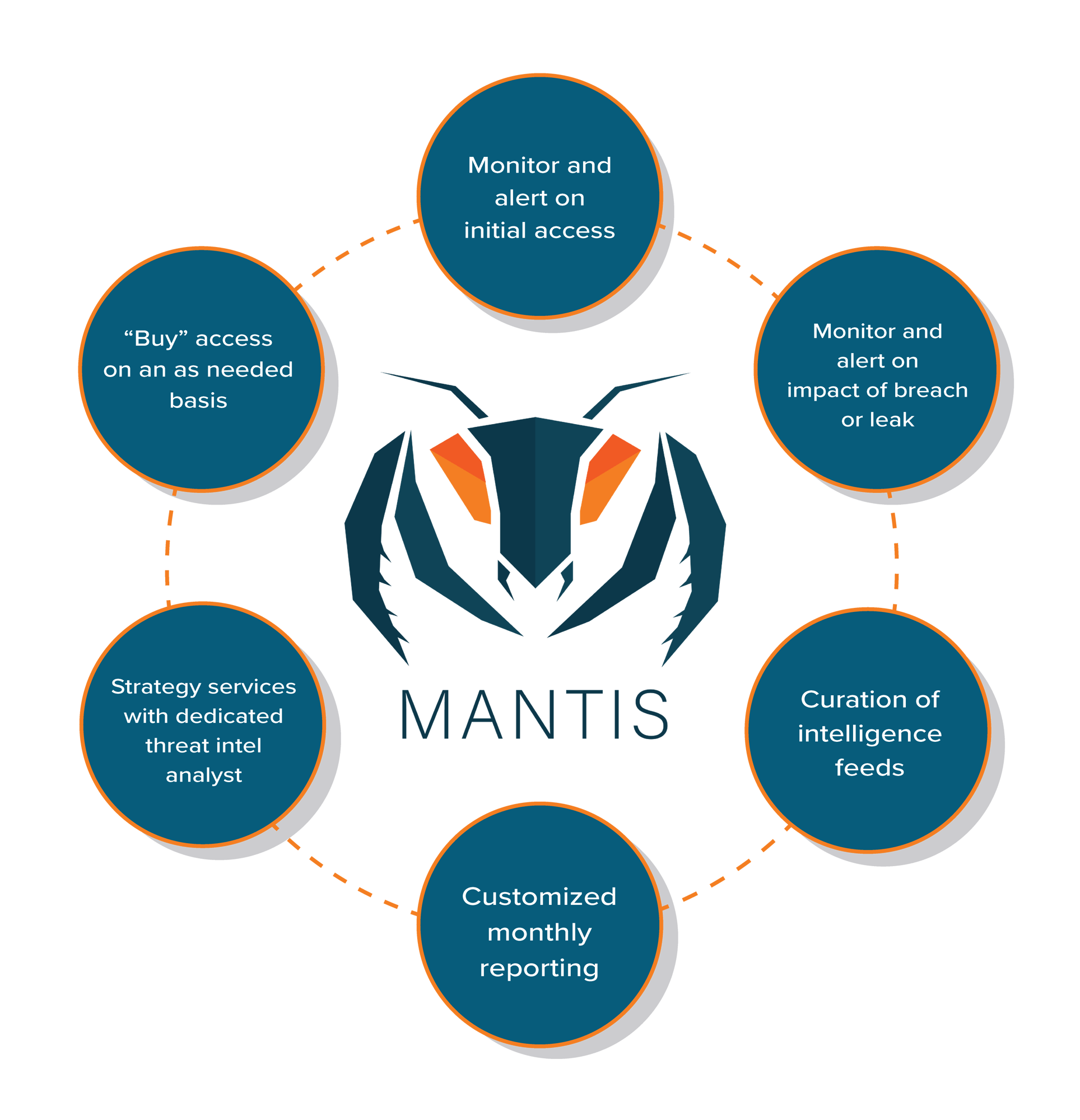
K logix's Managed Threat Intel Service
A low cost “Threat Intel Program in a Box":
- Our experts engage in strategic ways to reduce your exposure to threats before a breach
-
Monitor critical sources of intel
-
Provide analysis directly related to your industry
-
Increase maturity and protection with little to no impact on your team

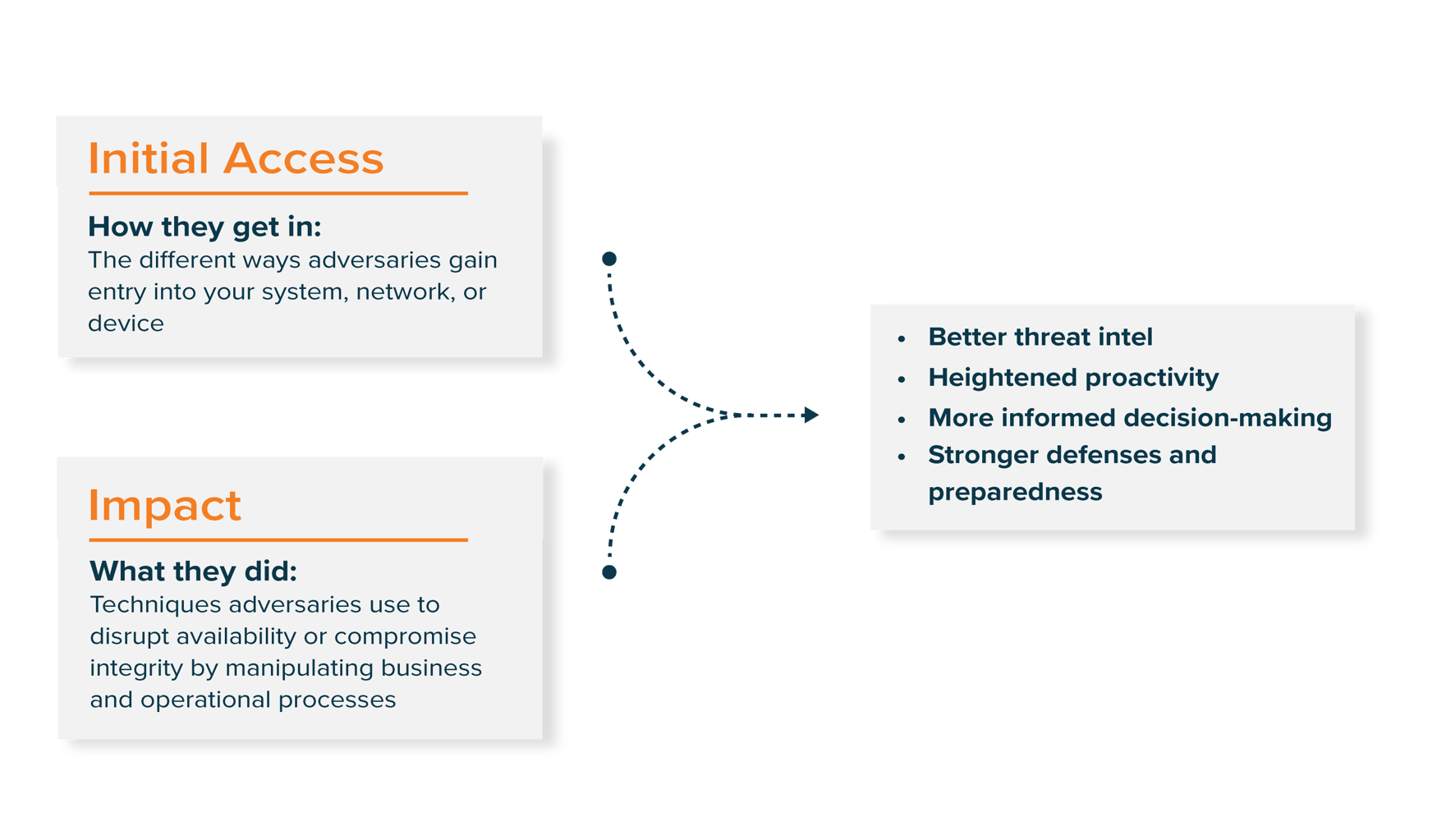
Intelligence Curation: Initial Access
K logix monitors initial access broker discussions and negotiations for any mention of client organizations. We notify key contacts at your organization and provide any situational awareness available.
Intelligence Curation: Impact
This includes domain monitoring of dark web posts, public notices and new stories for signs of breaches, and provide client notification when needed. K logix maintains access to one of the target's database of breached credentials and can review and analyze for critical user data.
Dedicated Threat Intel Analyst
Our Analysts act as your own threat intelligence team and will enrich your organization by providing: Threat Exposure Workshops, User Awareness Trainings, and Alerts or Quarterly Threat Review Reports.
Custom Reporting
Receive customized reporting specific to your organization and its goals related to threat intelligence. Reports are tailored for executive audiences, providing key content to reduce your risk.
Threat Intel is difficult, expensive and prone to signal overload
We provide curation of unique data feeds that deliver more signal and less noise
We include the people you need to start or augment your own threat intel program
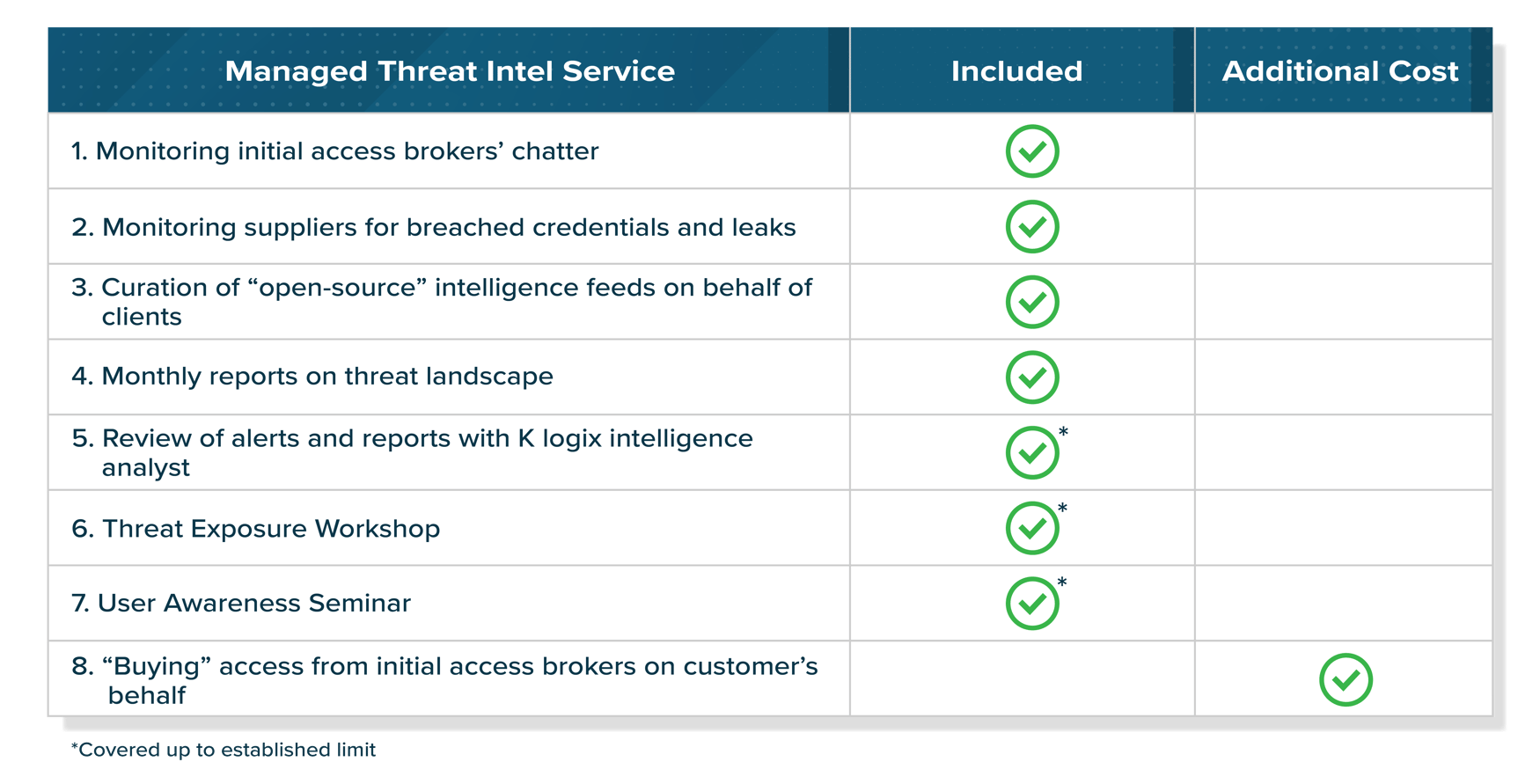
WHAT YOU RECEIVE
OUR APPROACH FOCUSES ON