.webp?width=2000&height=484&name=SmBanners-04%20(11).webp)

Cyber Research
Rapidly make a justified security product investment using K logix's vendor agnostic methodology.
We use a vendor-agnostic, risk-based and business case driven approach. The result is an analysis-backed, justified security product investment decision.
THE K LOGIX CYBER RESEARCH TEAM
The K logix Cyber Research team is made up of passionate and analytical thinkers who meticulously examine the cybersecurity technology marketspace. We take an agnostic approach by using our proprietary database to test and analyze security products based on extensive requirements, domains, and weightings. The dynamic nature of our analysis enables customers to use custom weightings of domains and requirements to determine the best fit technology based on their specific needs.ly

Save Time and Resources
We have done the work for you. Our experts produce results fast, saving your team valuable time.
Spend Budget Wisely
Budgets are not unlimited, we understand every dollar counts when investing in a new technology, and requires justification.
Align to the Business
Understanding what technology best fits your requirements is important, but then translating that so the business understands your decision is paramount.
> Read our Identity and Access Management Technology Advisory Case study.
We apply our Technology Advisory Methodology to any security area:
Application Programming Interface (API)
Attack Surface Management (ASM)
Automation
Cloud Native Application Protection Platform (CNAPP)
Data Governance
Data Loss Prevention (DLP)
Endpoint
Insider Threat
Identity and Access Management (IAM)
Mobile Device Management (MDM)
Managed Threat Detection (MTD)
Managed Security Service Provider (MSSP)
Network Detection Response (NDR)
Secure Access Service Edge (SASE)
Static Application Security Testing (SAST)
Segmentation
Security Information and Event Management (SIEM)
Third Party Risk
Vulnerability Management
Extended Detection and Response (XDR)
Zero Trust Network Access (ZTNA)
+ any other security technology area
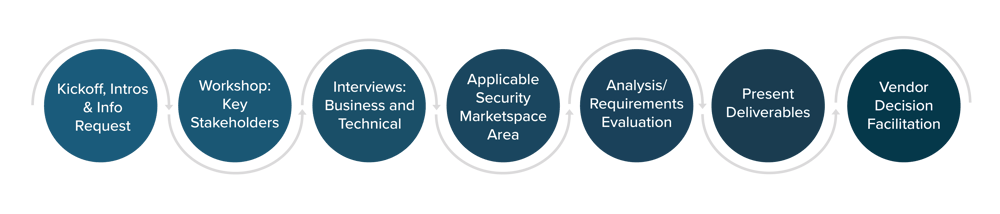
TECHNOLOGY ADVISORY PROCESS
TECHNOLOGY ADVISORY RESULTS
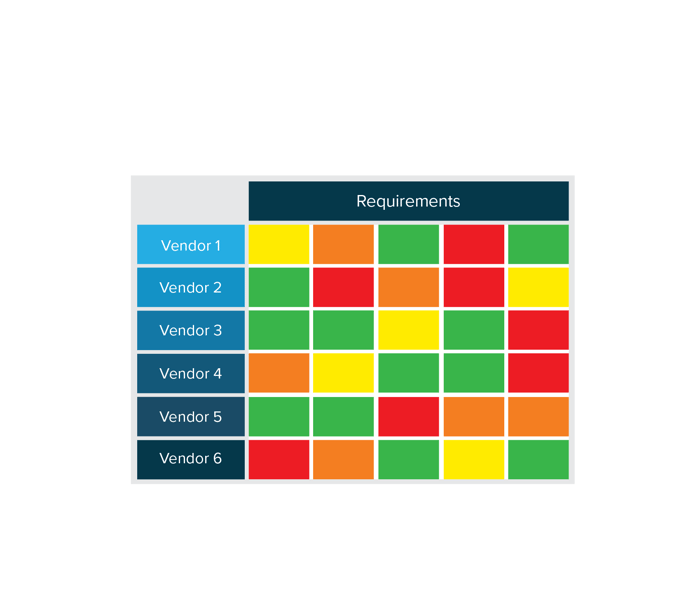
Heatmap
Identification of where products had critically different scores and which products meet (and miss) identified key requirements
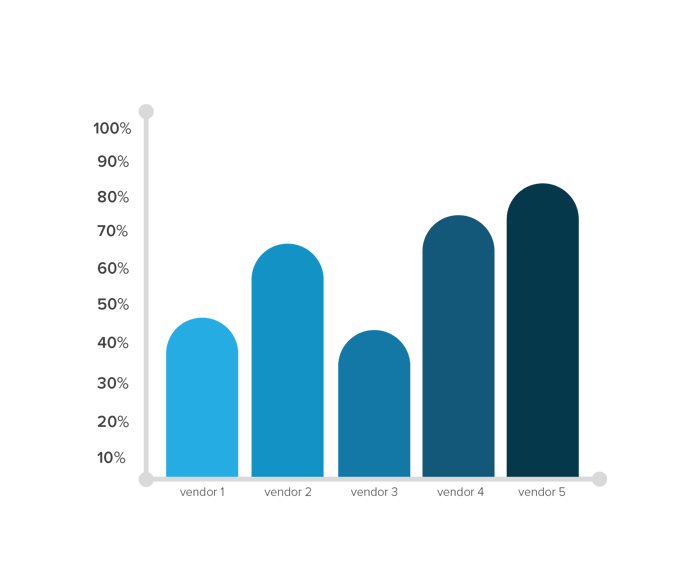
Technology Scoring
Graphs and charts that compare product scoring using weighted domains and requirements
Vendor Demos
Script and scorecard creation based on specific customer requirements, combined with facilitated vendor demos that speak directly to key requirements
BENEFITS
Cross-Functional Collaboration
We bring together business and technical stakeholders to determine appropriate requirements for product evaluation and ensure buy-in across the organization
Data-Driven Justification
From kick-off to final result, we deliver a justified, analysis-backed technology decision with data-driven visuals
Proven Methodology
We leverage our proven, repeatable methodology through workshops, interview sessions, and requirements analysis
Accelerated Time to Value
Leveraging K logix as an agnostic third party results in shorter timelines to a product decision
