Zero Trust
k logix understands the complexity and nuances around zero trust. we work with customers to deliver business-focused strategic security consulting and technology offerings to help address zero trust.
What We Offer:
K logix's white glove security consulting enables us to meet our customers where they are regardless of maturity. Our flexible offerings take into account business goals and security objectives to deliver results specifically tailored to customer requirements. Our offerings around Zero Trust include:
- Assessing your current Zero Trust program - determining alignment with a framework, measuring maturity, identifying gaps
- Building a Zero Trust program - formally documented strategy, assessment of current state, technology strategy and product recommendations
- Technology recommendations to fill identified gaps through our vendor neutral evaluation methodology
If you want to learn more about K logix's Zero Trust offerings, don't hesitate to let us know.
What is Zero Trust?
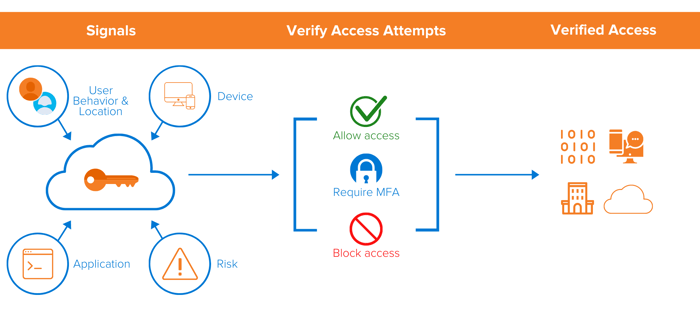
The Zero Trust Model challenges the traditional, perimeter-based “castle and moat” security model by changing the “perimeter” to anywhere within an organization where access control decisions occur. With a “castle and moat” security model, hackers do not meet much resistance moving inside internal systems. But, by following Zero Trust principles, security is ubiquitous within an organization as its users, devices and applications need to regularly re-establish trust to an organization’s assets.
While there is no single approach to Zero Trust Security, our latest Zero Trust blog post details guiding questions and useful steps that help security leaders decide how to best approach this method.
To better understand this concept, we asked our CISO community how they define Zero Trust, what it means to them, their approach and if it is achievable. To read their thoughts, please refer to our latest issue of Feats of Strength.

